K8S安装¶
1. 安装容器运行时¶
1.1 环境准备¶
- 配置免密登陆
ssh-keygen -t rsa -b 4096
ssh-copy-id 172.16.105.55
- 配置域名(hosts)
hostnamectl set-hostname
172.16.105.54 master01
172.16.105.55 node01
172.16.105.56 node02
- 时间同步
ntpdate ntp1.aliyun.com
- 禁用iptable和firewalld服务
systemctl stop firewalld
systemctl disable firewalld
systemctl stop iptables
systemctl disable iptables
systemctl stop NetworkManager
systemctl disable NetworkManager
- 关闭selinux
# vim /etc/selinux/config
SELINUX=disabled
# 临时关闭
setenforce 0
# 检查
getenforce
- 关闭swap分区
# 临时关闭
swapoff -a
# 永久关闭 vim /etc/fstab
sed -ri 's/.*swap.*/#&/' /etc/fstab
- 转发 IPv4 并让 iptables 看到桥接流量
cat <<EOF | sudo tee /etc/modules-load.d/k8s.conf
overlay
br_netfilter
EOF
cat <<EOF | sudo tee /etc/sysctl.d/k8s.conf
net.bridge.bridge-nf-call-iptables = 1
net.bridge.bridge-nf-call-ip6tables = 1
net.ipv4.ip_forward = 1
fs.may_detach_mounts = 1
EOF
sudo modprobe overlay
sudo modprobe br_netfilter
sudo sysctl --system
通过运行以下指令确认 br_netfilter 和 overlay 模块被加载
lsmod | grep br_netfilter
lsmod | grep overlay
通过运行以下指令确认 net.bridge.bridge-nf-call-iptables、net.bridge.bridge-nf-call-ip6tables 和 net.ipv4.ip_forward 系统变量在你的 sysctl 配置中被设置为 1:
sysctl net.bridge.bridge-nf-call-iptables net.bridge.bridge-nf-call-ip6tables net.ipv4.ip_forward
- 配置ipvs功能
yum install ipset ipvsadm -y
cat <<EOF> /etc/sysconfig/modules/ipvs.modules
#!/bin/bash
modprobe -- ip_vs
modprobe -- ip_vs_rr
modprobe -- ip_vs_wrr
modprobe -- ip_vs_sh
modprobe -- nf_conntrack_ipv4
EOF
chmod +x /etc/sysconfig/modules/ipvs.modules
/bin/bash /etc/sysconfig/modules/ipvs.modules
lsmod | grep -e ip_vs -e nf_conntrack_ipv4
1.2 安装containerd¶
- 下载containerd
从 https://github.com/containerd/containerd/releases 下载最新的containerd文件
# 安装前准备 容器挂载目录软链接
mkdir -p /data/containerd
mkdir -p /data/kubelet
ln -s /data/containerd /var/lib/containerd
ln -s /data/kubelet /var/lib/kubelet
$ tar Cxzvf /usr/local containerd-1.7.8-linux-amd64.tar.gz
bin/
bin/containerd-shim-runc-v2
bin/containerd-shim
bin/ctr
bin/containerd-shim-runc-v1
bin/containerd
bin/containerd-stress
配置自启动
# wget https://raw.githubusercontent.com/containerd/containerd/main/containerd.service
install containerd.service /etc/systemd/system/
systemctl daemon-reload
systemctl enable --now containerd
- 安装runc
从 https://github.com/containernetworking/plugins/releases 下载最新版的runc.cmd
install -m 755 runc.amd64 /usr/local/sbin/runc
- 安装cni插件
mkdir -p /opt/cni/bin
tar Cxzvf /opt/cni/bin cni-plugins-linux-amd64-v1.3.0.tgz
- 修改config.toml
mkdir -p /etc/containerd
containerd config default > /etc/containerd/config.toml
vim /etc/containerd/config.toml
-----
SystemdCgroup = false 改为 SystemdCgroup = true
# sandbox_image = "k8s.gcr.io/pause:3.6"
改为:
sandbox_image = "registry.aliyuncs.com/google_containers/pause:3.9"
-----
1.3 安装cri-o¶
- 配置镜像源
export KUBERNETES_VERSION=v1.28
export PROJECT_PATH=prerelease:/main
cat <<EOF | tee /etc/yum.repos.d/cri-o.repo
[cri-o]
name=CRI-O
baseurl=https://pkgs.k8s.io/addons:/cri-o:/$PROJECT_PATH/rpm/
enabled=1
gpgcheck=1
gpgkey=https://pkgs.k8s.io/addons:/cri-o:/$PROJECT_PATH/rpm/repodata/repomd.xml.key
EOF
- 安装
yum install cri-o -y
- 修改配置文件的pod网段
vim /etc/cni/net.d/11-crio-ipv4-bridge.conflist
{
"cniVersion": "1.0.0",
"name": "crio",
"plugins": [
{
"type": "bridge",
"bridge": "cni0",
"isGateway": true,
"ipMasq": true,
"hairpinMode": true,
"ipam": {
"type": "host-local",
"routes": [
{ "dst": "0.0.0.0/0" }
],
"ranges": [
[{ "subnet": "10.20.0.0/16" }]
]
}
}
]
}
- 启动
systemctl start crio.service
systemctl enable crio.service
1.4 安装cri-docker¶
下载最新的安装包 https://github.com/Mirantis/cri-dockerd
cd cri-dockerd
mkdir -p /usr/local/bin
install -o root -g root -m 0755 cri-dockerd /usr/local/bin/cri-dockerd
install packaging/systemd/* /etc/systemd/system
sed -i -e 's,/usr/bin/cri-dockerd,/usr/local/bin/cri-dockerd,' /etc/systemd/system/cri-docker.service
sed -i -e 's,SocketGroup=docker,SocketGroup=root,' /etc/systemd/system/cri-docker.socket
systemctl daemon-reload
systemctl enable --now cri-docker.socket
2. 配置集群¶
2.1 安装kubeadm¶
- 配置镜像
# 此操作会覆盖 /etc/yum.repos.d/kubernetes.repo 中现存的所有配置
cat <<EOF | sudo tee /etc/yum.repos.d/kubernetes.repo
[kubernetes]
name=Kubernetes
baseurl=https://pkgs.k8s.io/core:/stable:/v1.28/rpm/
enabled=1
gpgcheck=1
gpgkey=https://pkgs.k8s.io/core:/stable:/v1.28/rpm/repodata/repomd.xml.key
exclude=kubelet kubeadm kubectl cri-tools kubernetes-cni
EOF
- 安装
sudo yum install -y kubelet kubeadm kubectl --disableexcludes=kubernetes
sudo systemctl enable --now kubelet
sudo systemctl enable kubelet.service
- 配置命令补全
kubectl completion bash > /etc/profile.d/kubectl_completion.sh
- 配置endpoint
如果不设置端点,crictl会尝试连接到已知端点列表,这可能会影响性能。
echo "runtime-endpoint: unix:///run/containerd/containerd.sock" | tee /etc/crictl.yaml
- 配置集群
kubeadm init --control-plane-endpoint="172.16.105.54" \
--cri-socket /run/containerd/containerd.sock \
--kubernetes-version=v1.28.3 \
--pod-network-cidr=10.20.0.0/16 \
--service-cidr=10.21.0.0/16 \
--token-ttl=0 \
--upload-certs \
--image-repository=registry.aliyuncs.com/google_containers
- 配置环境变量
mkdir -p $HOME/.kube
sudo cp -i /etc/kubernetes/admin.conf $HOME/.kube/config
sudo chown $(id -u):$(id -g) $HOME/.kube/config
- reset
kubeadm reset -f --cri-socket /run/containerd/containerd.sock
rm -rf $HOME/.kube/config
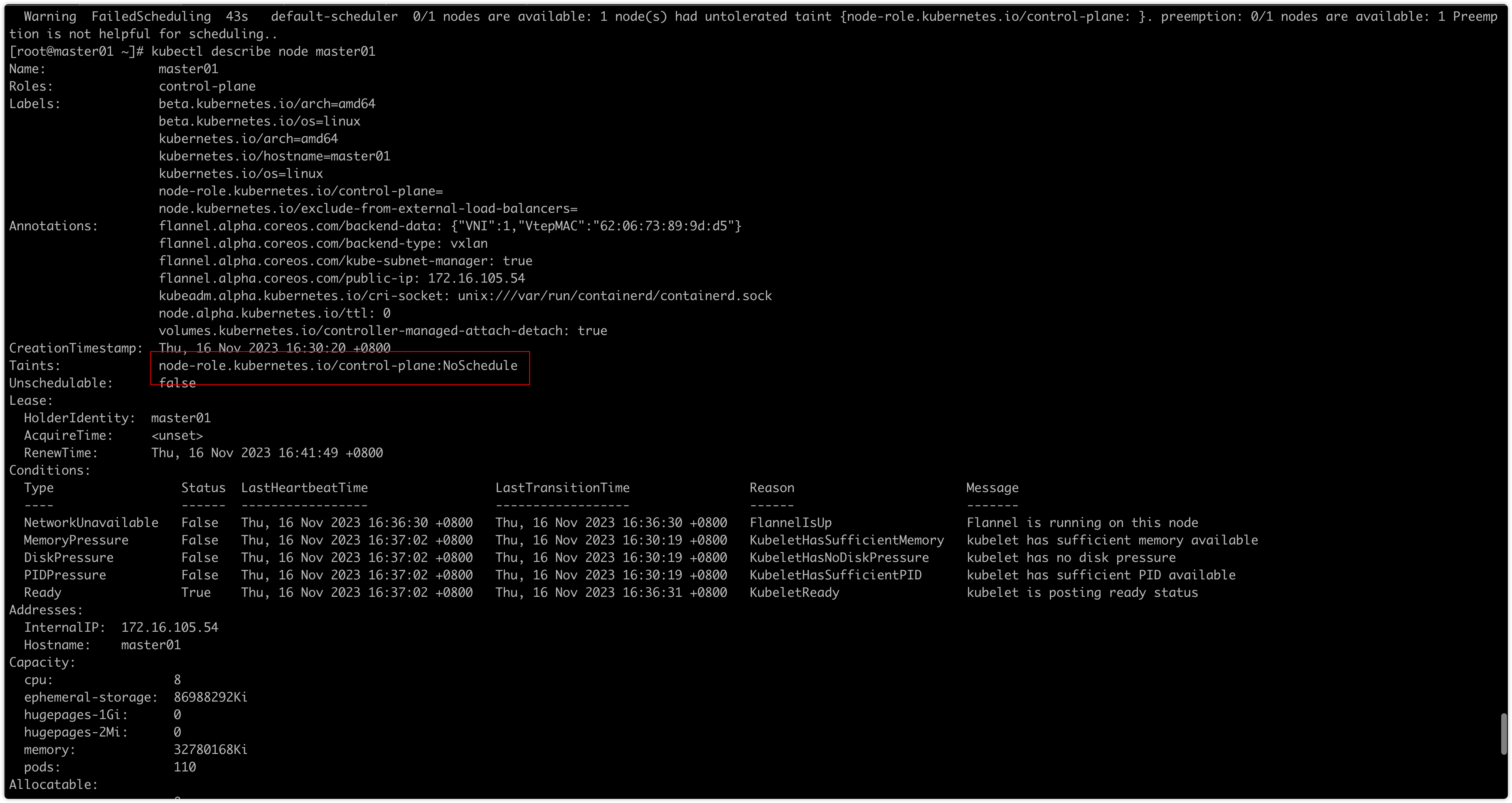
- 去除master污点
kubectl describe node master01
kubectl taint node master01 node-role.kubernetes.io/control-plane-
2.2 安装网络插件(flannel)¶
- 下载配置文件
wget https://github.com/flannel-io/flannel/releases/latest/download/kube-flannel.yml
- 修改配置文件
net-conf.json: |
{
"Network": "10.20.0.0/16",
"Backend": {
"Type": "vxlan"
}
}
2.3 添加节点¶
kubeadm join 172.16.105.54:6443 --token 2rp6dw.rsuyi69xlk6mnbgc --discovery-token-ca-cert-hash sha256:0ffb34f2817b8e9ed6ccb4e2e33b522a342a0a88841c21534627e5c1f4661b51 --cri-socket /run/containerd/containerd.sock